Workplace Preparedness: Getting Started

Pre-incident Planning: Be Aware, Be Prepared
- Download the UIC Safe app and become familiar with real time reporting and support resources, and additional features for a safer commute or for working alone on campus
- Watch the instructional video Are you UICReady? Surviving an Active Threat Event.
Knowing what to do can make the difference for you and those around you. - Review relevant evacuation procedures and identify the locations of fire alarm pull-stations, fire extinguishers, and emergency call boxes in the buildings you frequent.
- Identify secure hiding places in your immediate area(s).
- Identify multiple evacuation routes.
- Know your violence prevention resources: UIC Behavioral Threat Assessment Teams (BTAT) and your role in campus violence prevention.
- Review your Building Emergency Action Plan.
Links
Deans, Directors, and Department Heads
Deans, Directors, and Department Heads
- Ensure that your employees know these terms:
- Review and update your unit’s Continuity Plan.
- Develop a unit Emergency Notification and Communication Plan.
- Assign roles and responsibilities in your unit. Discuss what everyone will do and where they will go.
- Monitor credential systems, access control and badges; install badge-access checkpoints to prevent tailgating.
- Consider adding language to job descriptions such as “If you see something, say something to UIC Police in a timely manner.”

IN CASE OF AN ACTIVE THREAT EMERGENCY
- Report an emergency or suspicious activity to the UIC Police Department by dialing (312) 355-5555 (or 5-5555 from a campus phone) or by using the UIC Safe app.
- Obtain official emergency information from UIC Alert or uic.edu. The official UIC Twitter @ThisIsUIC may also be used as a trusted source.
- Misinformation is a significant risk and potential source of trouble in any fast-developing situation, so we urge all UIC affiliates to rely on only official university information.
- Follow instructions provided by UIC Alert or emergency personnel.
If you are not in the area of the active threat, but receive an active threat/shooter alert
If you are not in the area of the active threat, but receive an active threat/shooter alert
- Immediately lockdown your room unless otherwise directed by UIC Alert or emergency personnel.
- During a Lockdown Order:
1. Calmly, but quickly close and lock all doors into your room.
2. Block entry into your room, if possible.
3. Close and lock all windows in your room. Draw the blinds where possible.
4. Turn off the lights.
5. Hide in an area that is out of view and makes your location look as though it is empty.
6. Silence all electronic devices.
7. Remain as quiet as possible and attract as little attention to your area as possible.
8. Wait for further instruction from UIC Alert or emergency personnel.
9. Stay locked-down in your hiding place until you receive an “All Clear” message.
10. FACULTY/INSTRUCTORS: If you are teaching a class, say something along the lines of this message: “Attention everyone, we are being placed under lockdown. Please remain in this room and move to (an area in the room that is out of view). I am going to shut the lights off and lock and barricade the doors. Please silence your electronic devices. Let’s make it seem as if there is no one in this room. We will remain as quiet as possible and wait for further instruction.”
11. Call UIC Police by dialing (312) 355-5555 (5-5555 from a campus phone) if an emergency arises in your area. - Text your family to let them know you are okay.
- Closely follow the instructions of UIC Alert and emergency personnel.
Once the threat no longer exists: post-incident recovery
- You may be taken to UIC’s family reunification and assistance center, triage or other holding area for medical care, interviewing, counseling, or support services.
- Remain in secure areas until instructed otherwise.
- Once you have been evacuated you will not be permitted to retrieve items or access the area until law enforcement releases the crime scene.
- Do your best to support your own emotional needs and the needs of others; seek support for yourself and/or refer others to employee assistance and support resources accordingly.
- Stay in tune to updates on counseling services, relief, memorial activities, and other important news about the event.
For Deans, Director, and Department Heads:
- Account for all individuals you have oversight for.
- Employ continuity of operations plans to ensure mission essential functions are carried out.
- Coordinate with campus-level leadership in determining a transition plan that includes when to resume normal operations.
What to expect from responding UIC Police “contact team” officers
UIC Police “Contact Team” responding to an active assailant are trained in “rapid response” procedures and proceed immediately to the area on-campus in which shots were last heard; their mission is to stop the threat by locating the suspect in the most expeditious manner possible.
- Contact Team (Officers) may be armed with rifles, shotguns, and handguns
- Officers may aim their weapons at you
- Officers may use pepper spray or tear gas to control the situation
- Officers may be wearing regular uniforms, external bulletproof vests, Kevlar helmets and other tactical equipment
- Officers may shout commands and push individuals to the ground for safety
- Officers will NOT stop to render first aid or assistance to victims but may, where reasonably possible, inform them that additional rescue task forces are coming to assist and notify emergency responders of the victims’ locations and perceived conditions
- Rescue teams will follow shortly after the first responding officers enter the area. They will attend to the injured and evacuate everyone safely
- Regardless of how officers appear, remain calm. Do as the officers tell you, and do not be afraid of them.
- Put down any items in your hands (i.e., bags, jackets, backpacks, cell phones, etc.)
- Keep your hands visible at all times and spread your fingers
- Avoid making quick movements towards officers or grabbing a hold of them
- Avoid pointing, screaming and/or yelling at officers
- Do NOT stop to ask officers questions when evacuating, proceed in the direction from which officers are entering premises
- Keep in mind that once you have escaped to a safer location, the entire area is still a crime scene.
Source: The Safe School Initiative Report Prepared by the U.S. Secret Service and U.S. Department of Education
Characteristics of School Shooting Incidents:
- Incidents of targeted violence at school are rarely sudden, impulsive acts.
- Prior to most incidents, other people knew about the attacker’s idea and/or plan to attack.
- Most attackers did not threaten their targets directly prior to advancing the attack.
- There is no profile of a student attacker.
- Most attackers engaged in some behavior, prior to the incident, that caused others concern or indicated a need for help.
- Most attackers had difficulty coping with significant losses or personal failures.
- Many attackers had considered or attempted suicide.
- Many attackers felt bullied, persecuted, or injured by others prior to the attack.
- Most attackers had access to and had used weapons prior to the attack.
- In many cases, other students were involved in the attack in some capacity (in over half of the incidents others assisted in planning or execution of attack by actively encouraging the attacker to shoot others at school, helping select targets, and training a shooter how to use a weapon).
Personal Security Considerations, Behavioral Indicators
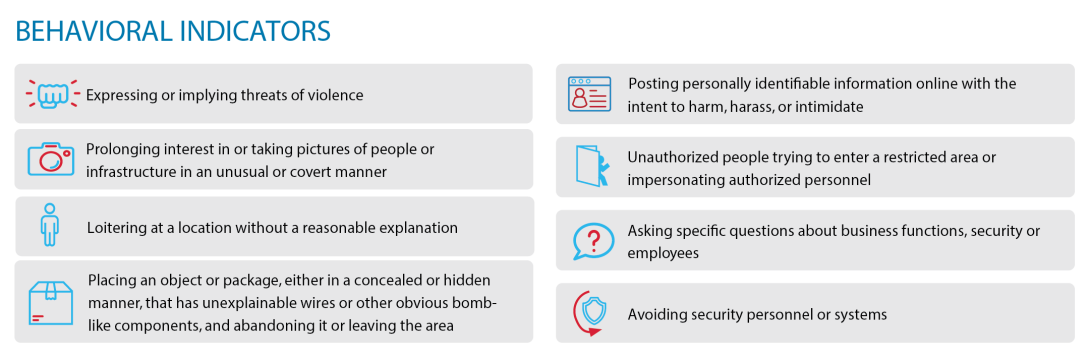
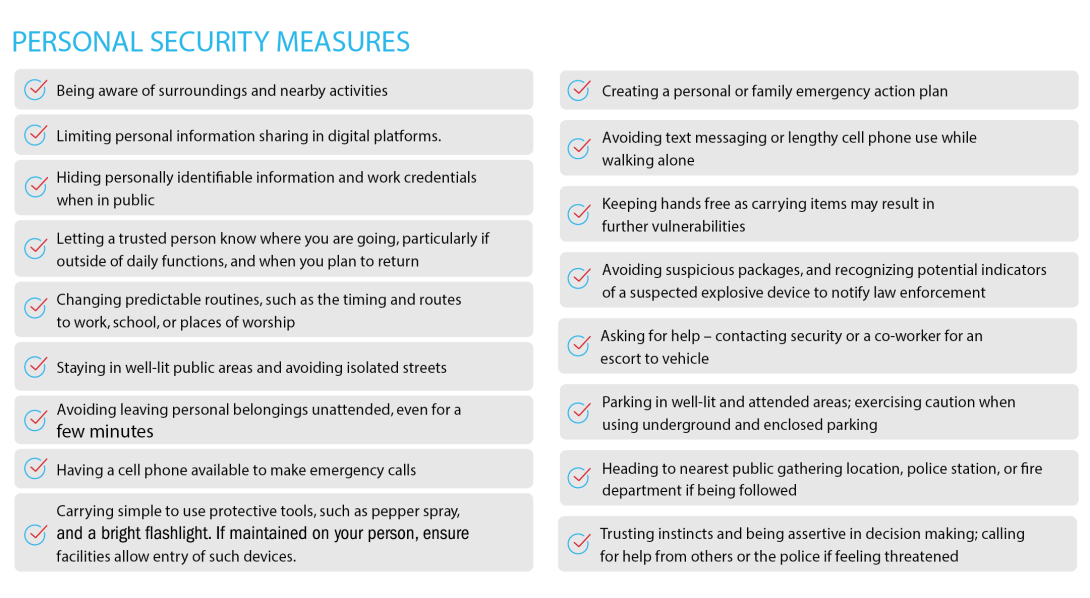
The CISA Personal Security Considerations fact sheet identifies behavioral and suspicious activity indicators and provides basic personal security measures to reduce the probability of becoming a victim of an attack.
Behavioral Indicators
PERSONAL SECURITY MEASURES
Pathway to Violence
The “Pathway to Violence” video provides information regarding the behavior indicators that assailants often demonstrate before a violent act.
Download the printer-friendly Pathway to Violence fact sheet that explains warning signs that may lead to violence and what individuals can do to mitigate a potential incident.
Continuity Planning
With the goal of helping your class, laboratory research, or business operations better prepare to minimize disruption of service and maintain normal operations during an emergency or crisis, the UI Ready Continuity Planning tool to help your department/unit generate a plan tailored to your specific needs.
The Power of Hello

Used effectively, the right words can be a powerful tool. Simply saying “Hello” can prompt a casual conversation with unknown individuals and help you determine why they are there. The OHNO approach – Observe, Initiate a Hello, Navigate the Risk, and Obtain Help – helps employees observe and evaluate suspicious behaviors, and empowers them to mitigate potential risk, and obtain help when necessary.
This approach describes activities and behaviors that may be suspicious or indicative of criminal activity. These activities may be constitutionally protected and should be reported only when there are articulable facts to support a rational conclusion that the behavior is suspicious. Do not report based solely on protected activities, race, religion, gender, sexual orientation, or a combination of only such factors.
The Cybersecurity and Infrastructure Security Agency (CISA) site provides stakeholders with information to assist in identifying and effectively responding to suspicious behavior.
